Mac Tips: FileVault
Enabling Full-Disk Encryption

Most people don’t realize that the default settings their computer comes with is not set up very well from a security perspective. In fact the stock Mac configuration is intentionally generic and accessible so that it works easily for everyone right out of the box. One simple way to improve your Mac’s security is to enable the full-disk encryption that comes built into macOS.
There is no reason not to encrypt your hard drive; especially on a mobile device like a laptop. With full-disk encryption if somebody steals your computer they can’t get access to your documents, photographs, bank account information… etc. Apple includes FileVault, their implementation of full-disk encryption on macOS 10.7 Lion and later. It’s an easy to use and effective product that could save you worry should your machine be stolen; all you have to do is turn it on.
FileVault is a one time setup. To turn it on you just click the button, restart, and wait a few hours for the program to encrypt all your old data in the background. You can continue using your device as it is being encrypted and all future data will be encrypted automatically.
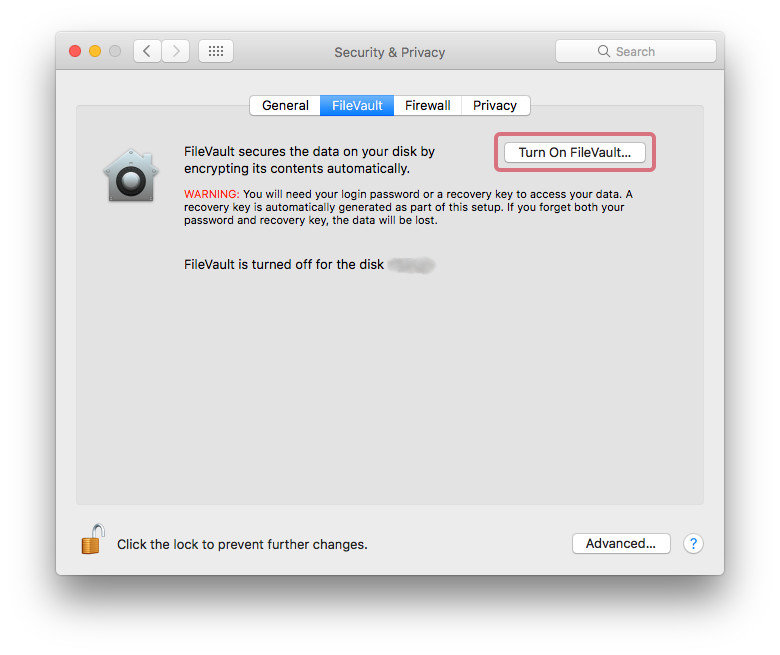
To turn on FileVault Encryption go to:
System Preferences > Security & Privacy > FileVault
and click “Turn on FileVault”.
Warning: We strongly recommend keeping your recovery key in a safe and separate location. Forgetting your password and losing your recovery key will render all of your data permanently unretrievable.
Another important element for best practices is password quality and that will be getting its own dedicated post very soon. In the meantime, let us know if you have any questions on other default software settings that may be leaving you vulnerable.
Advanced
If you’re familiar with the command line and are comfortable with using some python you can use this script: osx-config-check. It goes through a list of changes to similar default security settings as the one above and allows you to pick and choose. It does a lot of the heavy lifting for you, but not every ‘check’ is right for everyone so I don’t recommend aiming for 100% compliance. Your machine still has to be useable afterwards
As always, you should be critical of code before running it on your computer. In the case of Open Source code on GitHub you can often get a good idea of its legitimacy by looking at the changes that have been made and how popular it is.
